Chevy Chase, Maryland 20815 Wisconsin Ave, Suite 700
Serious investment, casting wealth
Asia’s most international multi-asset exchange, trusted by the public, operates securities, fixed income and derivatives markets with the highest regulatory standards.
- Benefit from fast execution and low costs
- Expand your investments and achieve global diversification for profitable results.


Why You Choose Our
trading platform
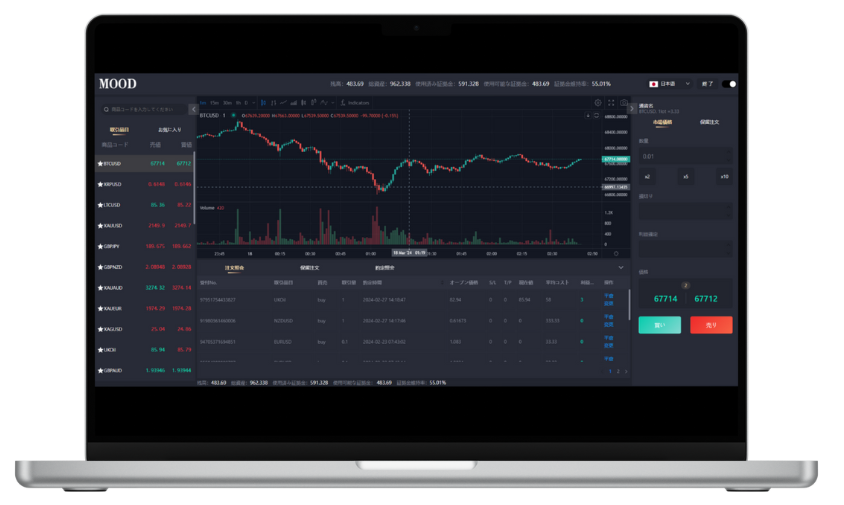
Mobile trading make easy
Every user controls the data they wish to see as well as the dashboard's structure.
Powerful trade matching engine
High-performance matching engine with ultra-low latency, large throughput, no jitter, and no downtime during peak times.
Socially responsible
Fixed income, cryptocurrencies, and equities trading platform with stringent regulatory oversight
Security & control over money
Swift, Reliable, Your Financial Shield—Safeguarding Assets with Robust Securit
K
Active Installation
K
Active Members
K
Active Installation



Frequently Asked Questions
If you need to install a specific software, you just need to follow the instructions in the app store.
We take the security and privacy of user data very seriously. We have implemented various security measures to ensure the protection of your personal information, including encryption techniques, secure protocols, and more. You can rest assured that your data is safe when using our app, and we are committed to continuously ensuring its security.
As part of our commitment to maintaining a secure environment for our users, we employ several measures to secure our servers. These include regular security audits, implementing firewalls, employing encryption protocols, conducting routine software updates and patches, and closely monitoring server activity for any signs of unauthorized access or unusual behavior. Additionally, we ensure that only authorized personnel have access to the server infrastructure. Our goal is to continuously assess and enhance our server security to safeguard our users' data and privacy.
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between a trusted internal network and untrusted external networks, such as the internet. Firewalls are used to establish a secure perimeter, preventing unauthorized access to or from private networks while allowing legitimate communication to pass. Firewalls are utilized to protect networks and systems from various types of cyber threats, including unauthorized access, malware, viruses, and other malicious activities. By implementing a firewall, organizations can control and filter network traffic, thereby enhancing overall security and reducing the risk of potential cyber attacks.
Get in Touch
support@igjp.site